We continue to focus our attentions on this growing, highly concerning risk, and discuss out the box solutions that can effectively tackle this steading increasing concern, to every organization in the world.
In recent studies it has been concluded, that the following are some of the key issues that need to be understood more comprehensively by C-Suite and Senior Management.
- The average cost of a single data breach is approximately $4.5 million per incident;
- The average cost of recovery from a ransomware can be in the ballpark of $2.7 million, (+- R49 million);
- Downtime and consequential business interruption and disruption, experienced by companies, on average has gone from days to weeks, in some incidents up to months, post a ransomware attack;
- The cost of this crime is set to exceed $10 Trillion by 2025 – this is big business for the criminals!
What are then some of the key drives that are contributing to this growing risk? Well the top 3 contenders could be as follows:-
Advancement in technology
- If we consider the growth trajectory of the adoption of the internet and cloud, the graph will look as below. The adoption we see today occurred over decades.
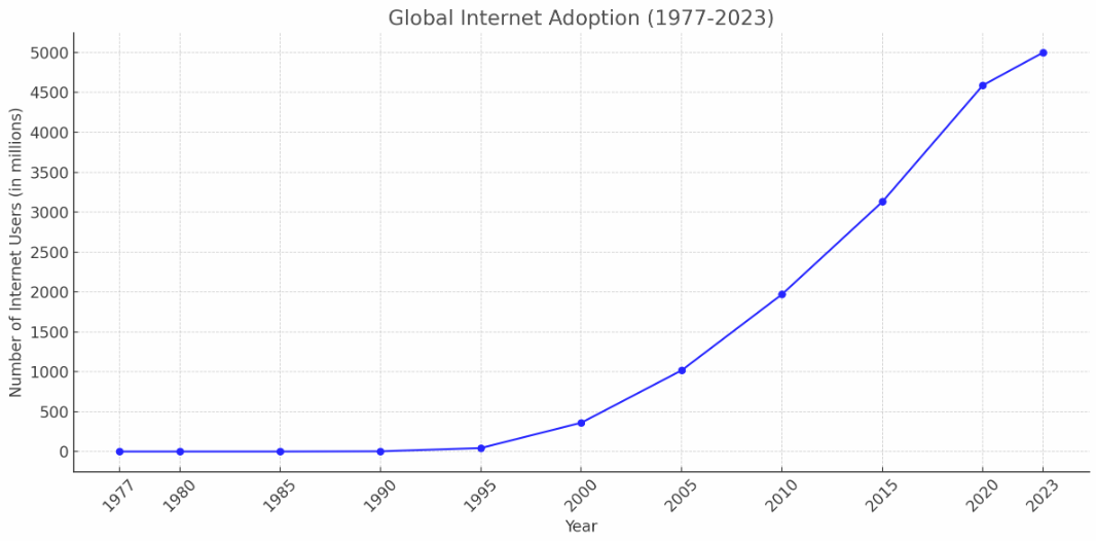
Image 1: Internet adoption graph over time
- If we consider the trajectory of the adoption of AI since the significant explosive introduction of Chat GPT in November 2022, (according to OpenAI, ChatGPT acquired 1 million users just 5 days after launching). The adoption was terrifyingly rapid and the world was using AI in every daily activity almost overnight. There are an estimated 6.9 billion smartphone users worldwide, all of which now use AI in standard features.
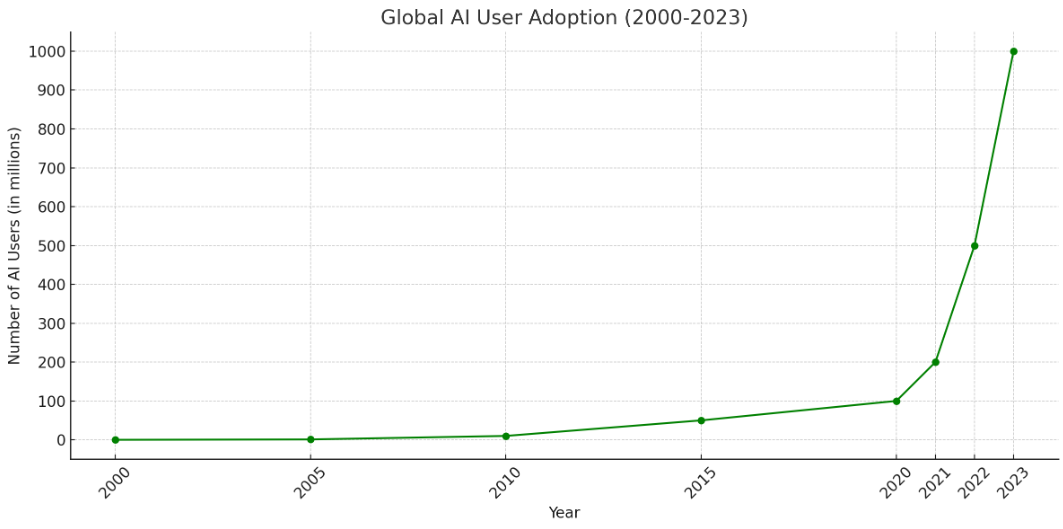
Image 2: AI as usual Adoption over time
Increased connectivity – a world online
- It is estimated that a little over 2 thirds of the world population is consistently on line
Sophistication of the Threat Actor
- The level of sophistication of the threat actor is deemed highly likely to achieve success in any given attack launched
- Ransomware as a Service is readily available on the Dark Web
- Significant funding is readily available to sophisticated Threat Actors on the Dark Web
- Regulatory frameworks related to digital currencies are still in early stages and yet to be fully matured
- Organizational training and awareness is still too weak to combat the level of skills the Threat Actors possess
Taking into account the above 3 key drivers, it is simply no longer a question, that organizations have to up their game in developing strategies to combat this risk.
The Rise of Cyber Risks – Unpacking some of the Root Causes in Specific Case Studies
Before we go about discussing solutions to this question, let’s spend a minute unpacking 3 significant cyber and information security events, of recent times, to fully understand how these events came about.
The 3 case studies we shall address are as follows:
- Equifax Data Breach (2017)
Overview: The Equifax data breach is one of the most significant data breaches in history, affecting approximately 147 million individuals. Equifax, one of the largest credit reporting agencies in the United States, announced the breach on September 7, 2017.
- The How? – Known Vulnerabilities exploited – The attackers exploited a known vulnerability (CVE-2017-5638) in the Apache Struts web application framework. This vulnerability was disclosed and patched in March 2017, but Equifax had not yet applied the patch. The attackers used a specific technique to gain initial access to Equifax’s network, by exploiting the unpatched vulnerability. Once inside the attackers simply did what they needed and wanted to encrypt data and exfiltrated it with zero “knowledge” on Equifax’s part, despite several alarms that went off, where Equifax failed to act on the security warnings.
- The Impact – The breach, which exposed the personal information of approximately 147 million people, including Social Security numbers, birth dates, addresses, and in some cases, driver’s license numbers and credit card numbers, led to widespread public outcry and a severe loss of trust in the company. Equifax faced fines and penalties and several lawsuits, with settlements in excess of $500 million, to assist people affected by the data breach. The breach led to the resignation of multiple C-Level executives. The reputational damage was significant and lasting.
- Could it have been prevented? – Yes (Effective Patch Management / Effective Monitoring / Proactive rapid response to Alarms with effective incident response management / Diligent IT Management and eradication of weak internal controls / improved employee internal awareness and training / better governance and oversight in place)
- MOAB Data Breach (2024)
Overview: The MOAB (Mother of All Breaches) data breach of January 2024 is one of the largest and most complex data leaks in history, involving over 26 billion records. This breach is not the result of a single cyberattack but rather a compilation of data from multiple sources, including previous data breaches and data enrichment activities.
- 26 Billion Records breached
- Multiple data sources, including data from previous data breaches
- Multiple countries / sectors / government organizations / online platforms (LinkedIn / Canva, Dropbox / Adobe)
- Massive volumes of PII – opening the door to Identity theft / financial fraud / extortion / further cyber attacks
- The How? – Data Aggregation Services & 3rd Party Risks – The breach was primarily due to a misconfigured server at a data breach search engine called Leak-Lookup, which inadvertently exposed this massive dataset to the public. The server was vulnerable due to insufficient access controls and security weaknesses.
- The Impact – The exposure of such a large amount of data has significant implications for privacy and security, the world over. Affected individuals and organizations are at increased risk of phishing attacks, identity theft, and other forms of cybercrime, as a result of the breach. The full consequences of the breach are still unfolding, but it highlights the critical need for robust cybersecurity measures and the risks associated with data aggregation services and services provided by 3rd parties.
- Could it have been prevented? – Yes (Effective Good IT Health Management and Best practices / Control Assurance measures oversight on configuration management / encryption methods applied to at rest and in transit data / access control and multi-factor authentications / ISO 27001 and other best practice standards certifications). In summary, the Leak-Lookup data breach underscores the critical importance of implementing and maintaining strong cybersecurity measures to protect sensitive information and maintain user trust. It is an interconnected world where the security universe transcends outside of your own back yard.
- CrowdStrike (19 July 2024)
Overview: The event on the 19th of July brought a large percentage of the Western World to its knees in an unprecedented outage event due to a failed software update executed in a manner that was nothing short of gross negligence. The software update failure involved a problematic update to CrowdStrike’s Falcon platform. The specific update caused massive, “unexpected” issues that affected the functionality of the software, leading to disruptions for users on Microsoft / Google platforms that led to outages across the world.
- Over 5000 cancelled flights globally;
- Major hospitals had to halt surgeries and other critical services;
- Banks and other financial institutions experience intermittent processing and transactional delays / panic in consumers who could not draw cash;
- General Business relying on Microsoft Azure and Google Compute Engines faced system reboots and crashes / downtime and extensive IT support impacts to restore normal operations. This includes department stores and groceries stores using cash registers / schools computers, business using the Falcon CrowdStrike software;
- Warnings from cyber security agencies that threat actors are taking advantage of the incident;
- A lot of questions to be answered as to how one single software update could bring much of the Western World to a grinding halt!
- Market share loss for CrowdStrike was significant and Competitor advantage is still to be seen in the months to come.
- The reputational damage we know from history, will be with CrowdStrike for years to come.
- The How? – A Coder’s error in a Software update not detected through an effective Quality Assurance Process – Anyone in the software development industry will be scratching their heads for some time to come on how this basic 101 in a quality testing and deployment process error could have made it to a production environment.
- The Impact – This event is the most significant consequential waterfall event in recorded history. The consequences were endless and affected volumes of organizations around the world in service disruptions, loss of services, potentiality in fatality and health issues as hospitals had to halt surgeries and other critical services. The reputational damage to not only CrowdStrike, but Microsoft and other multiple organizations that were affected by the incident and its consequential damages. Many questions still to be asked and answers given.
- Could it have been prevented? – Yes (Standard comprehensive software testing best practices / Effective and monitored dev – test – deployment processes / Software Engineering Best Practices applied / ISO Standards and other best practices alignment and assurance over enforcement of controls).
In Conclusion
Looking at the preventive measures, in each of the 3 case studies above, that should have been in place and the gargantuan dearth of governance and oversight that seemed to have existed, one has to ask the question, is there a more effective preventative solution strategy?
If we now circle back to the explosion of AI and consider how AI can in fact be a highly effective tool as a preventative measure in combating cyber risks and information security incidents, in terms of our 3 case studies.
We have spoken at length in our Blog of last month, as to ways in which AI Augmented risk and control techniques, can be very effectively used in addressing continuous control and risk monitoring. Click the link here if you didn’t catch last months Blog, Harnessing The Power Of AI For Internal Controls Monitoring And Evaluation (rubiqbiz.com).
If we take the 3 case studies above and look at how Transactional Data Based GRC, could have been used in each of these scenarios.
- Equifax
- Policy is first needed, that clearly makes statements on evidence that would need to be produced as proof of effectiveness of control, would have highlighted the Key Risk Indicators as follows:
- No critical systems are left unpatched – Algorithms and available AI models can be used to ensure that a full body of knowledge can be brought to Managements attention, using plain English narratives, that explain the exact nature of the risk and the recommended actions to be taken. Thus, not leaving the decisions on what might be considered routine IT housekeeping, to be swept aside, but providing an opportunity for critical business decision makers to engage in preventative risk decision making, with AI translating the risks into simple consumable language.
- Policy is first needed, that clearly makes statements on evidence that would need to be produced as proof of effectiveness of control, would have highlighted the Key Risk Indicators as follows:
- MOAB Data Breach and the CrowdStrike Incident
- Critical IT controls continuous monitoring. Key Risk indicators as follows:
- All controls identified in terms of a standard Statement of Applicability monitored by algorithms against effective and efficient enforcement rules. The Human being cannot process millions of transactions, records and data points, but AI can. The key lies in the algorithm and more specifically, how that “if Statement” is precisely defined and the data that the algorithm is put on top of.
- Critical IT controls continuous monitoring. Key Risk indicators as follows:
We are revolutionizing our clients insights through AI Augmented GRC solutions daily and the difference is clear and easy to see.
If you would like more information about how we can assist your continuous improvement strategy in effective IT Governance, click the link below.
Interested in a Case Study on GRC Augmented with AI within a real business context? Click the link to download the case study.
Are you concerned about how exposed you are to cyber risks and the potential of data breaches, click the link to get a free quote to conduct a Cyber Security Maturity Benchmark Evaluation.





