How Simple Good IT Practices Could Have Prevented Major Cyber Attacks, Data Breaches, and Ransomware Events!
In the last 24 months, the world has witnessed several high-profile data breaches and cyberattacks that have compromised sensitive information, disrupted operations, and caused substantial financial and reputational damage. While these incidents often make headlines, what’s less frequently discussed is how many of them could have been easily prevented through basic IT practices, adherence to standards and best practice frameworks, like ISO 27001, NIST CSF 2.0 and CIS v8.0, etc. supported by effective governance of IT.
The Basics: What Went Wrong?
The common thread running through many of these incidents is not just a lack of proper IT housekeeping, but overall good governance and a human failure to effectively interpret the warnings or act and quickly respond to the warnings. From outdated software and weak passwords to poor network segmentation, lack of due diligence to act and respond, in an agile manner, perhaps due to insufficient employee training, many organizations have left themselves exposed to attacks that could have been easily avoided with standard best practices. We covered a few high-profile case studies in our July Blog last month on just this topic. Here are a few more studies for your consideration, where the consequences of the IT good practice failures were significant.
Breaches That Could Have Been Prevented
1. Colonial Pipeline Ransomware Attack (May 2021)
The Colonial Pipeline attack was one of the most disruptive ransomware incidents in recent history, leading to widespread fuel shortages across the Eastern United States. The root cause?
A single compromised password linked to an inactive VPN account. The account lacked multifactor authentication (MFA), a basic security measure that could have easily prevented the attackers from gaining access to the network.
Information Technology fundamentals, that are addressed under the ISO 27001:2022 standard, that really should have been in place:
- Implementation of multifactor authentication for all accounts, especially those with access to critical systems.
- Regularly review and disable inactive accounts.
- Conduct routine penetration testing to identify and close potential vulnerabilities.
- Regular Business Impact analysis assessments, within the context of the organization.
- Risk insights analysis taking the context of the organization into account, evaluated along with employee performance appraisals, the IT landscape, human behaviour analysis, control assurance over the last 6 months at least.
What often is in place are the aspects related to the first 3 bullet points above, the last 2 bullet points we rarely, if ever find to be in place, yet the last 2 are critical in an effective Cyber and Information Security defense strategy.
2. JBS Foods Ransomware Attack (June 2021)
JBS Foods, one of the largest meat processing companies globally, was brought to a halt by a ransomware attack that targeted its North American and Australian operations. The attack reportedly exploited outdated software that had not been patched, a common issue that many organizations overlook.
So, what should have the IT Department of JBS Foods been doing to prevent this event?
- Establish a robust patch management program to ensure all systems are updated with the latest security patches.
- Prioritize critical vulnerabilities based on the potential impact on operations.
- Automate updates where possible to reduce the risk of human error.
- Implement an effective IT Internal Audit process supported by AI augmented continuous evaluation, of all transactional data, through transactional data-based audit tooling.
Through the effective implementation of an ISO 27001:2022 management system, supported by a team that understands the interrelationship between people > processes > systems and technology, this event would potentially never have happened at JBS Food. We often take for granted, as a tick box compliance exercise, a simple diagram of the interaction between ISMS processes, and don’t stop to think about how to enable improved security through clear understanding of process interrelationship, and thus create a transparent harmony through such processes, in addressing the flow of information through an organization:-
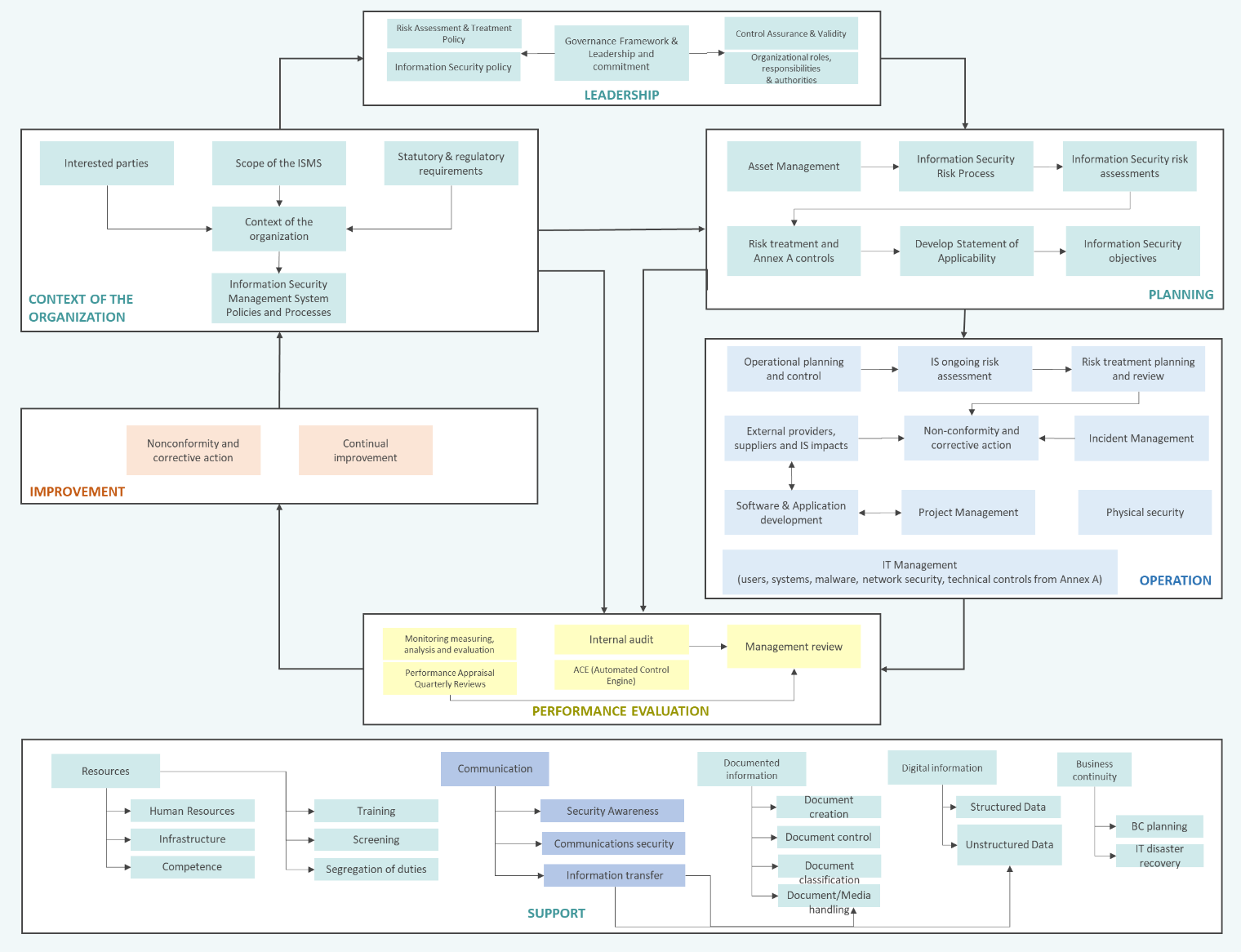
3. Marriott International Data Breach (2020)
In 2020, Marriott International suffered a data breach that exposed the information of 5.2 million guests. The breach was traced back to the credentials of two employees being compromised. Weak access controls and a lack of segmentation within their network allowed attackers to move laterally and access sensitive data.
Easy Prevention Measures that the Marriott IT Team could have taken:
- Enforce strict access controls and ensure that only authorized personnel can access sensitive data.
- Implement network segmentation to limit the movement of attackers within the network.
- Regularly audit user access rights and modify them as roles and responsibilities change.
Had the Marriott IT Team really taken the time to just apply and adopt, through the organization, the integrated process diagram above, through enforcement of their Information Security, Privacy and Cyber defense controls, they well may have never realized this risk.
The Role of ISO 27001 in Preventing Breaches
ISO 27001:2022, the international standard for information security management, provides a comprehensive framework for securing sensitive information. The standard outlines key controls and best practices that, if implemented correctly, can significantly reduce the risk of breaches and other related information security and cyber risks: (some key controls include the below bullet points)
- Risk Assessment and Treatment: Regularly identify and assess potential risks, and implement controls to mitigate them.
- Information Security Policies: Develop, adopt and enforce policies that govern how data is handled and protected within the organization.
- Access Control: Ensure that access to sensitive information is restricted to authorized personnel only, and is based on the principle of least privilege.
- Incident Management: Establish a robust incident response plan to quickly detect, respond to, and recover from security incidents.
- Continuous Monitoring and Evaluation: Establish an effective and agile continuous control and assurance system, that monitors the entire IT landscape, within both the structured and unstructured data arenas, and drives risk detection, and an effective daily road to green remedial journey.
Conclusion: The Need for Effective Governance and Control
While sophisticated attacks are becoming alarmingly more common, many of the breaches and ransomware incidents we’ve seen could have been easily prevented with basic IT practices. Organizations must prioritize good IT housekeeping, implement security standards like ISO 27001, and establish strong governance and control assurance frameworks, to protect themselves against the growing threat of cyberattacks.
By adopting these measures, companies can significantly reduce their risk and ensure that they are not the next headline-making breach. With the average cost of a breach in South Africa between 5 and 50 million rand, the key takeaway is simple: prevention is far more effective and less costly than remediation.
We have assisted many clients through an effective and efficient sequential ISO 27001 certification journey, that makes all the difference in the maturity level of each business we have worked with.
If you would like to get ISO 27001 certified or improve your IT GRC strategy, contact us by clicking the links below.
Interested in a Case Study on GRC Augmented with AI within a real business context? Click the link to download the case study.
Are you concerned about how exposed you are to cyber risks and the potential of data breaches, click the link to get a free quote to conduct a Cyber Security Maturity Benchmark Evaluation.





